Skip to collection list
Skip to video grid
Trending
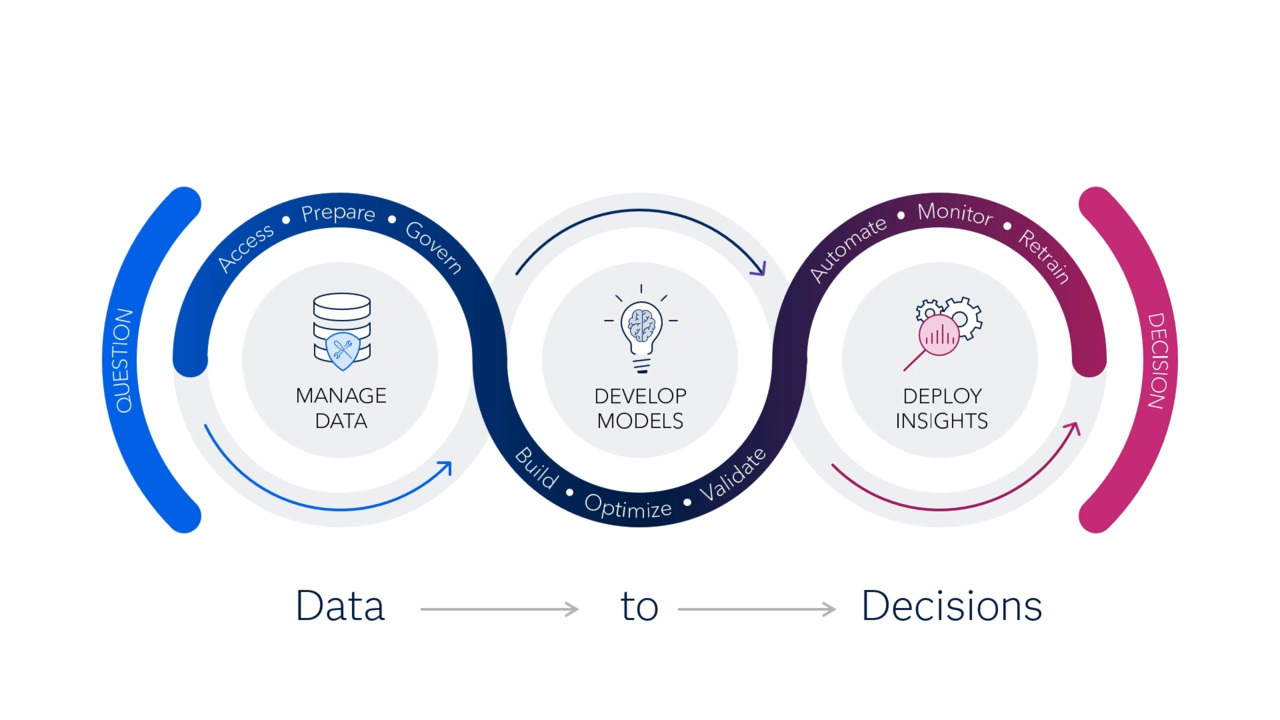
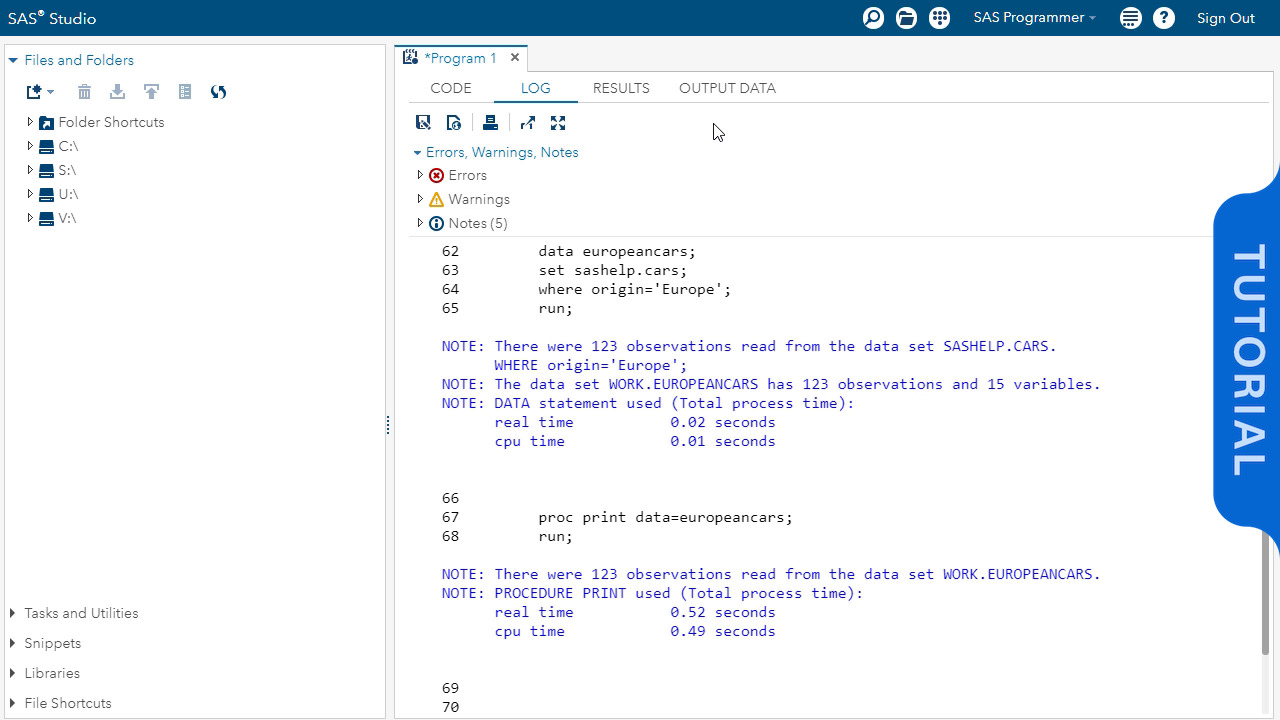
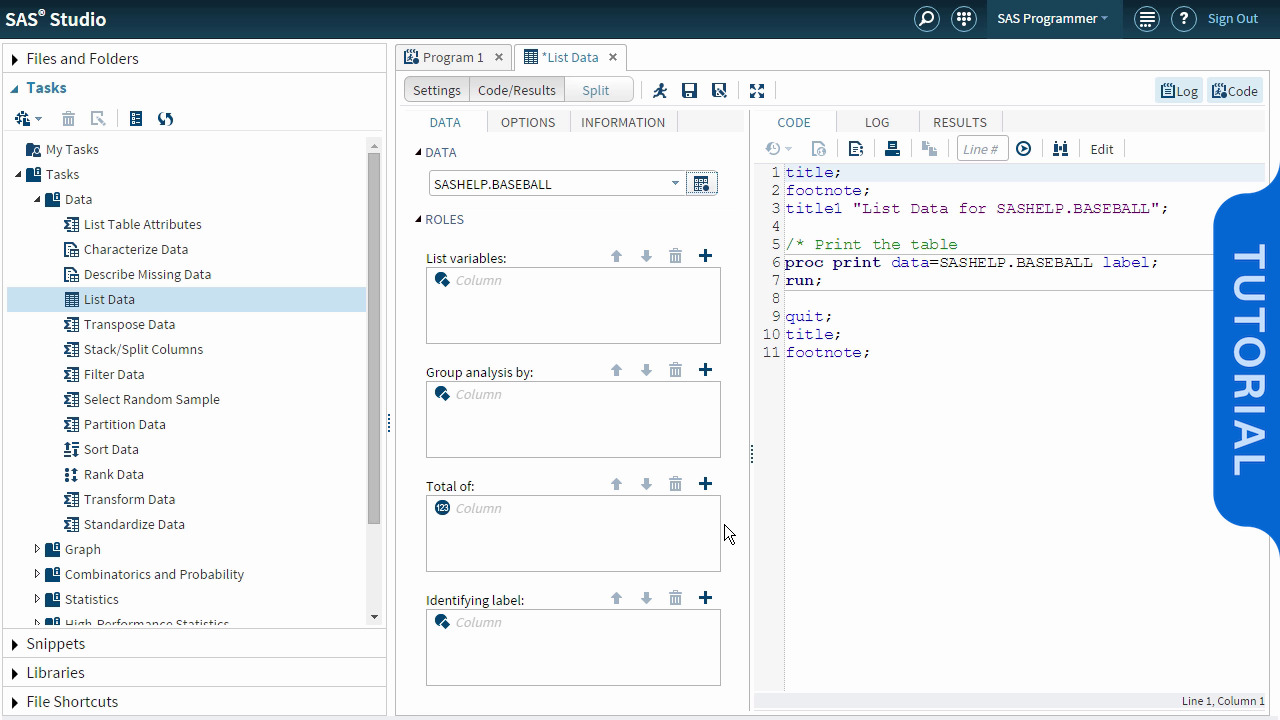
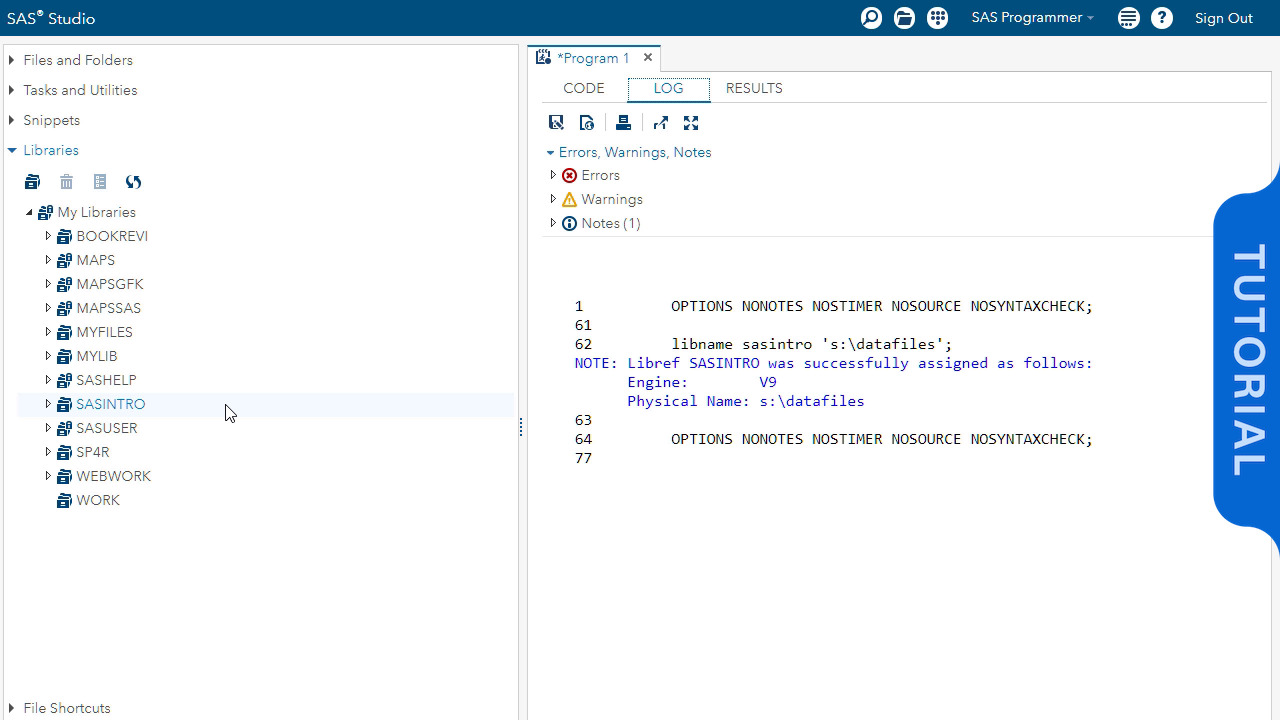
Kerberos Authentication Process
We examine the messages passed between components and how the different encryption keys we review last time get used in practice. We look at both the initial authentication of the user and how the user then authenticates to a service.
Read More
Read Less